According to Group-IB, this could be a sign that GoldPickaxe is targeting Vietnamese users. “Based on the specific requirement of face scanning, along with the fact that GoldFactory is operating in the region, we suspect that they may have started deploying GoldPickaxe in Vietnam,” Group-IB stated.
In a warning about online scams issued by the Department of Information Security under the Ministry of Information and Communications in February, there was a case of a user in Hanoi being tricked into installing fake public service software. The software requested a video verification, and the next day, the user’s securities account was sold and billions of dong were transferred out.

An iPhone being used for face scanning. Photo: Luu Quy
The presence of GoldPickaxe at a conference on finance and banking in Ho Chi Minh City in mid-March also raised concerns among organizations. According to Troy Le, representative of BShield, a security tool developer supporting many major applications in Vietnam, this malware is dangerous because it has been successfully exploited on both iOS and Android platforms, while also collecting biometric data of users. As Thailand has implemented biometric authentication, including facial recognition, for large transactions, and Vietnam is also about to apply this method, GoldPickaxe becomes a new challenge for users and platforms in protecting accounts.
How does GoldPickaxe infiltrate accounts?
First, the attackers will try to get the victim to install the malicious application on their device through social engineering techniques. In the case of the Hanoi victim mentioned above, they impersonated a government agency to trick the user into installing the fake public service software. In Thailand, common scenarios involve tax refund and electricity bill payment assistance software.
For Android devices, users only need to install the application through an apk file. Meanwhile, for iOS, attackers will exploit Apple’s application testing platform, TestFlight, or convince the victim to install a Mobile Device Management (MDM) profile, giving them full control over the device.
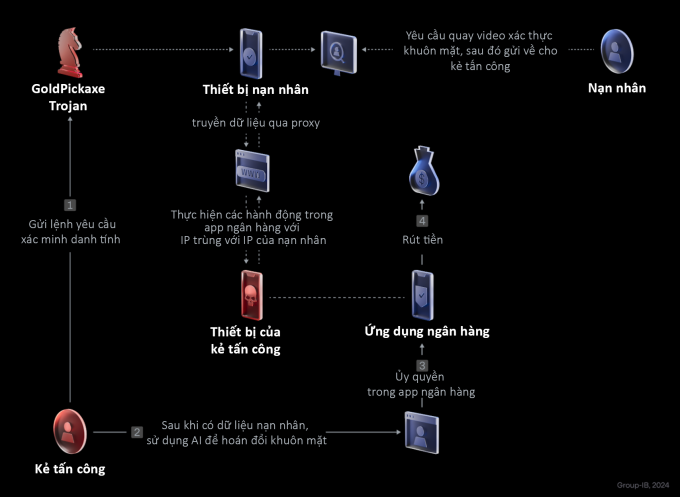
Attack mechanism of GoldPickaxe. Source: Group-IB
Once inside the device, GoldPickaxe activates certain privileges, such as SMS filtering and internet access. At the same time, the fake application will ask the user to verify their identity with personal documents and a video recording. This video is sent to the hacker’s server, becoming material for deepfakes, face swapping using AI.
According to expert Troy Le, the malware will quietly collect personal information from the device and secretly record data on the user’s activities and inputs, creating log files. Additionally, it also collects facial data and possibly the victim’s IP address to mimic their behavior, thereby tricking services into believing it is the genuine user.
“With this data, the attacker does not need to directly perform illegal transactions from the victim’s phone. Instead, they collect all the necessary information to access the user’s banking application from another device,” said Troy Le.
How to stay safe from GoldPickaxe?
The Department of Information Security has continuously issued warnings and recommendations for users to not provide personal information or install applications from unknown sources to prevent account theft. However, in reality, attack scenarios and methods are constantly changing, causing many people to fall victim despite being cautious.
From the perspective of a security platform developer, Troy Le believes that banks and financial organizations also need to take proactive measures to protect their users.
After implementing BShield for many financial and banking applications in Vietnam, Troy Le pointed out that some platforms and services still have weaknesses, such as lacking a mechanism to detect unsafe devices and take timely preventive actions, and lacking continuous monitoring during the application’s operation. This allows hackers to take control of the victim’s account once they pass the initial verification stage. Additionally, some applications may have API vulnerabilities, allowing malware to interfere and modify the application’s behavior, enabling man-in-the-middle attacks.
“Financial and banking applications are always the primary targets of hackers. Therefore, they need to establish mechanisms to protect both their users and their services,” the expert recommended.
According to Group-IB, the malware from the GoldFactory group also has many features that can trick users, such as fake application alerts, fake call screens, and deceptive messages prompting the victim to perform certain actions. Users should be cautious if they notice any unusual behavior, such as rapid battery drain, unusual device heat, strange notifications, high data usage, or applications requesting excessive permissions.