Why is Personal Data Protection Important?
The internet has led to an increased risk of information insecurity. Personal accounts are easily hacked, invaded, and leaked, and scams on social networking sites like Facebook are on the rise. Recent incidents like the Zoom app hacking have made it clear that personal data is not secure. Therefore, it is more important than ever to protect personal data.
Personal data is a valuable asset of the digital economy. It is used in various fields such as administration, healthcare, law enforcement, and identity verification. Therefore, it is crucial to maximize the security of personal data.

Avoiding impersonation: If personal data is hacked, it can lead to impersonation and fraudulent activities, which can have a severe impact on one’s image and life. It is important to be cautious with personal information such as email address, phone number, social media profiles, credit card information, and home address.
How to Check if Personal Data and Information Have Been Leaked?
Step 1: Access the website of the National Cyber Security Monitoring Center – NCSC at https://khonggianmang.vn/
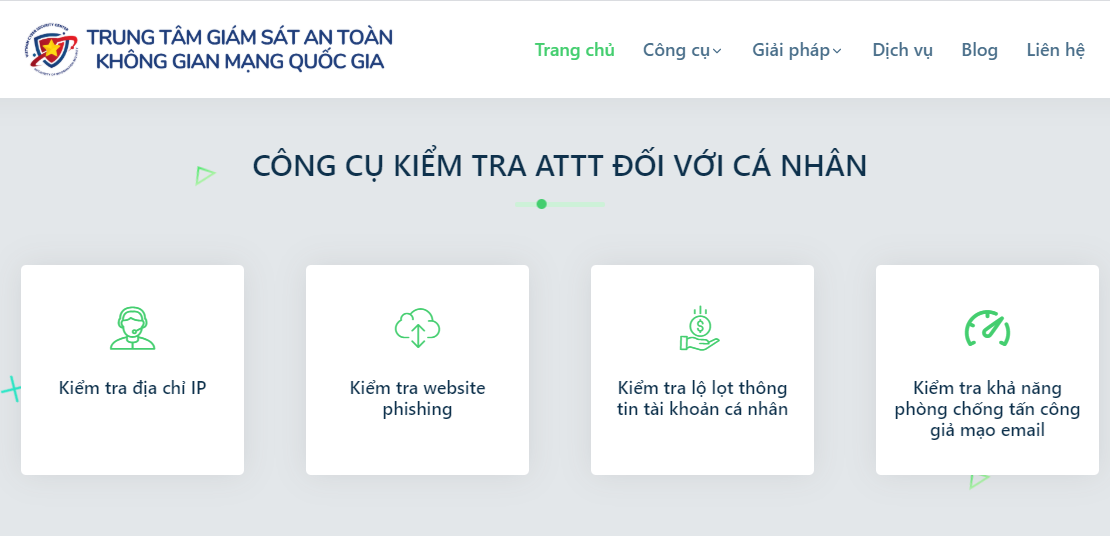
The website provides tools for individuals to check their information security. These tools include:
- Check IP address
- Check phishing websites
- Check leaked personal account information
- Check the ability to prevent email spoofing attacks
Check IP Address
This tool helps you check if your Public IP address has connected to any botnet network in the last 30 days. You can click on the “Check IP address” section on the homepage.
Click on the “Check” button to get the results.
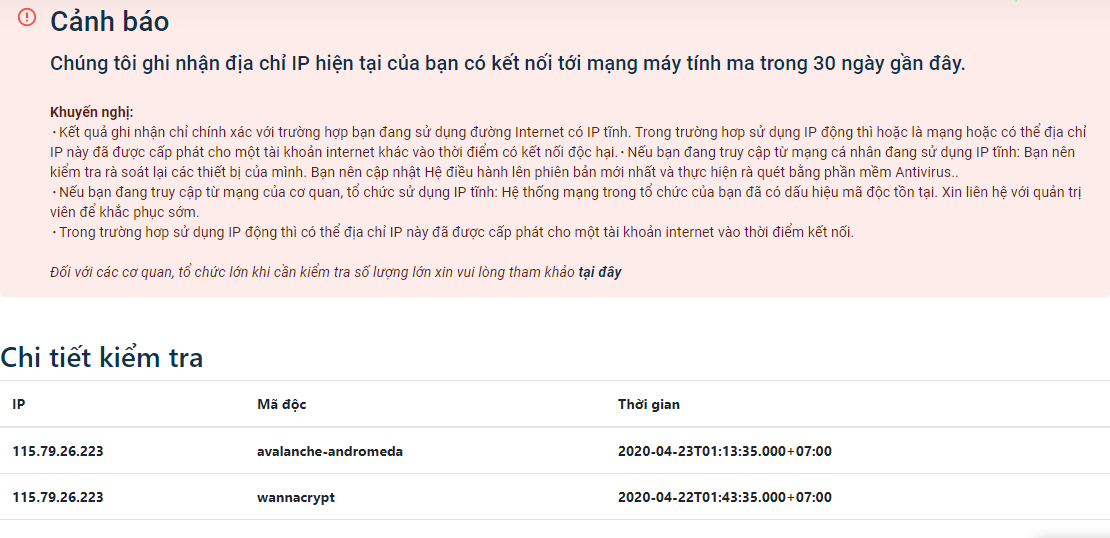
The system will display the results immediately.
Check Phishing Websites
This tool helps you check if a suspicious website is a scam. Simply click on “Check phishing website”.
Enter the link of the website you want to check into the “Enter URL” field.
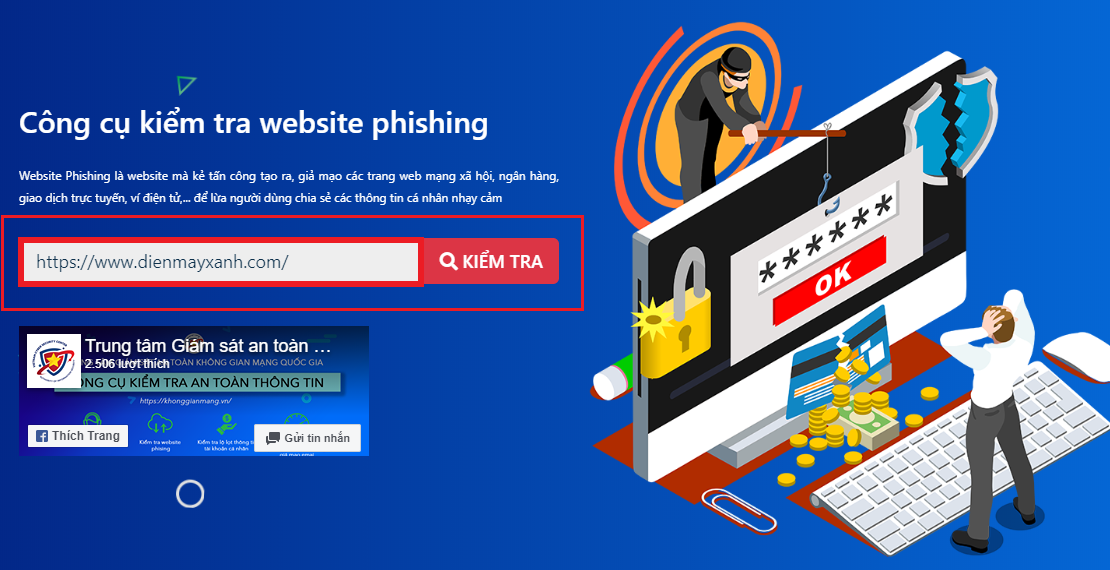
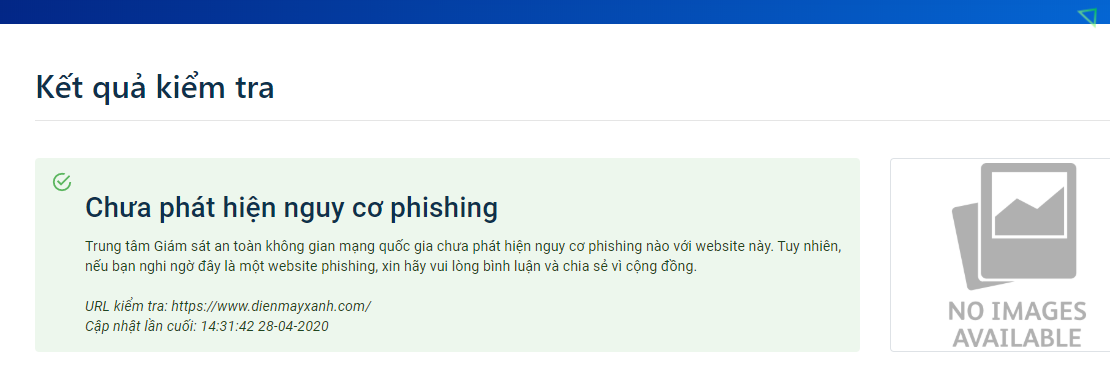
The results will be displayed below.
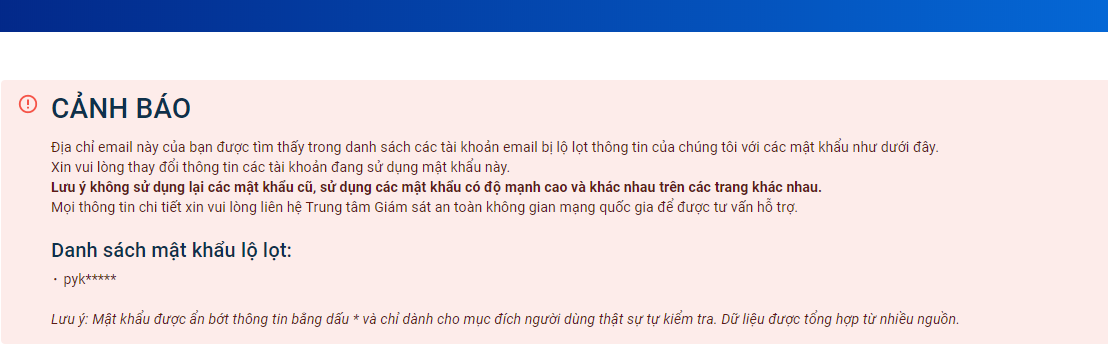
Check Leaked Personal Account Information
This tool helps you check if your personal accounts have been leaked on the internet. Click on “Check leaked personal account information” to start checking.
Enter your email and click on “Check”.
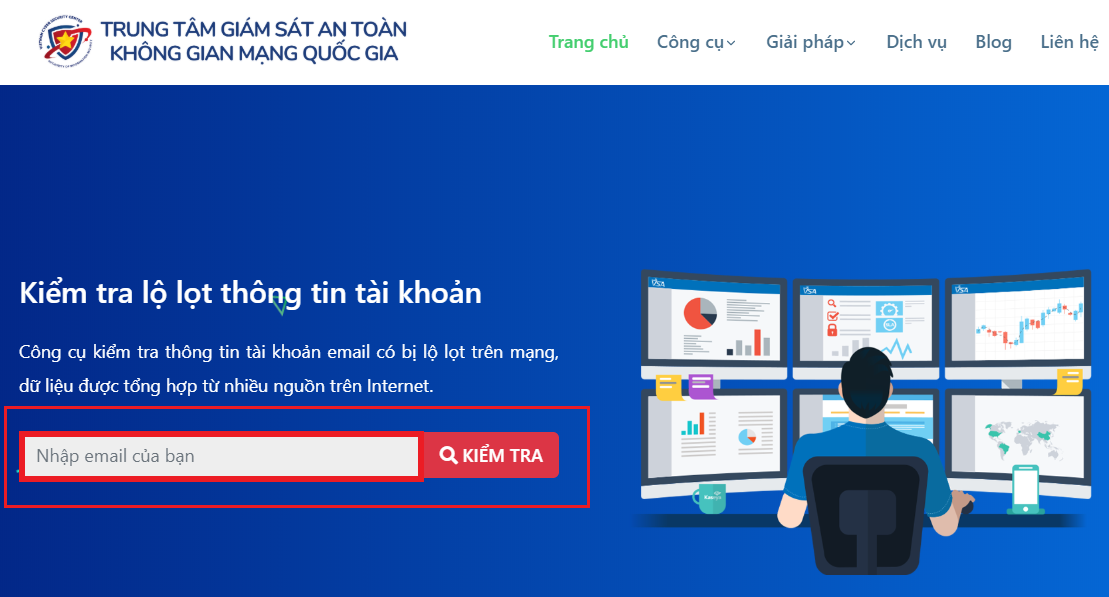
The results will show if your email address is found in the list of leaked email accounts. If it is, it is advisable to change the account’s information and password.
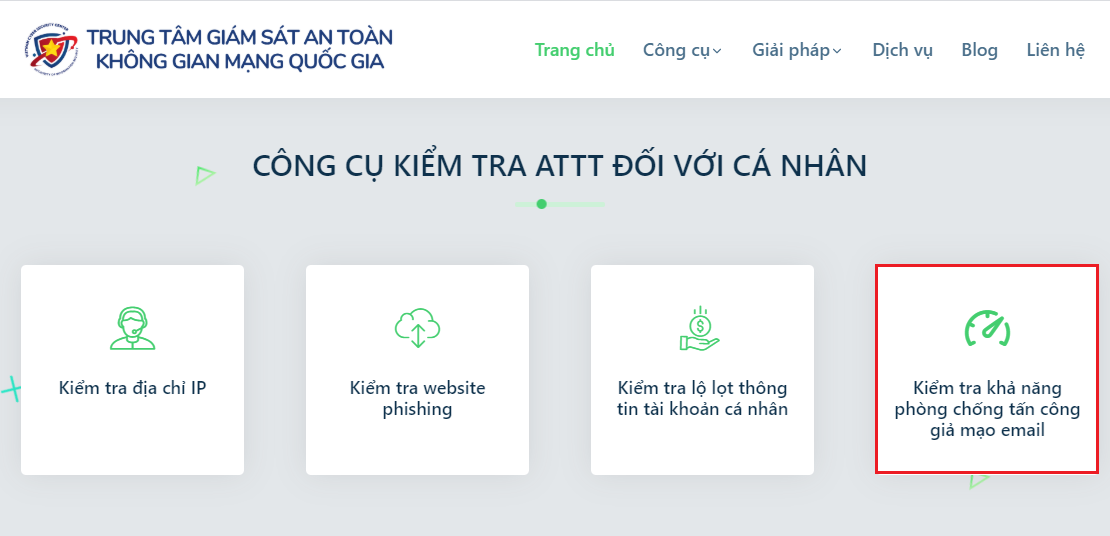
Check the Ability to Prevent Email Spoofing Attacks
This tool allows you to check if your company/organization’s email address has the ability to prevent phishing attacks.
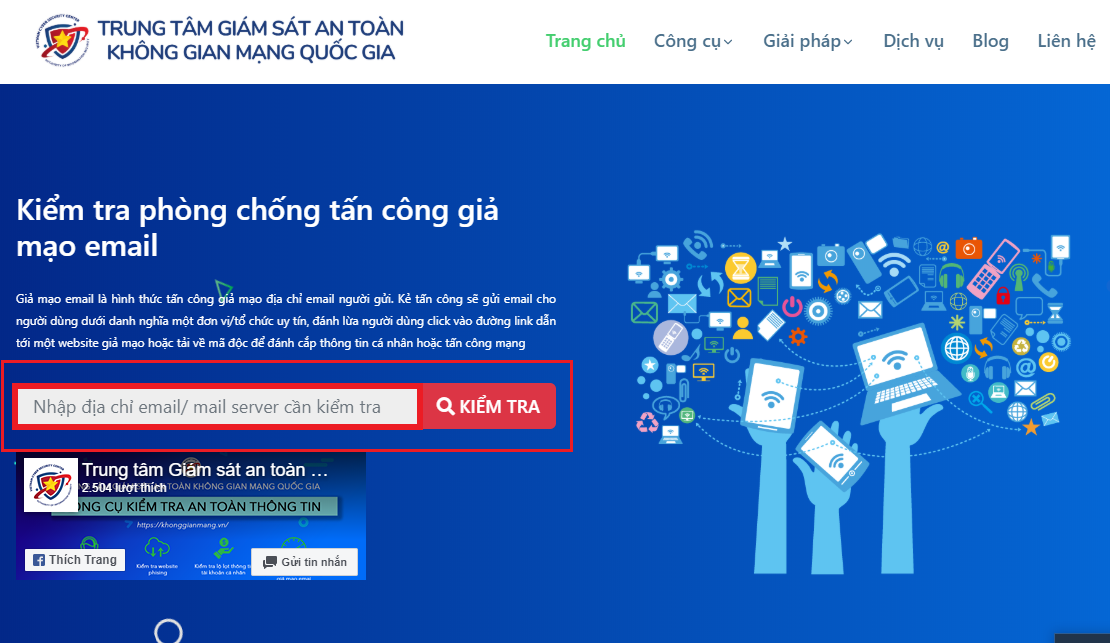
Enter your email or email server address to check, and then click on “Check”.
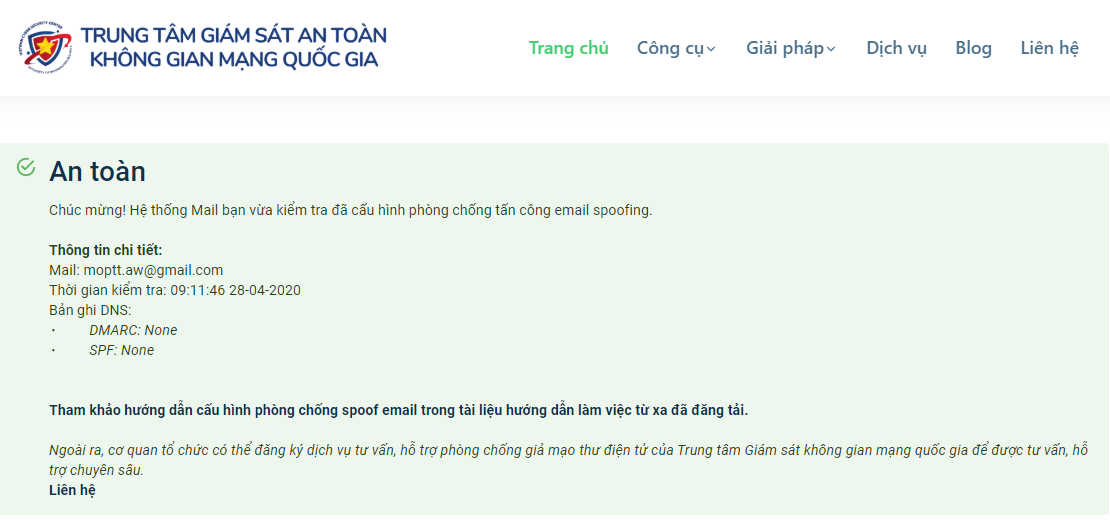
The system will warn you if the sender of the email is a phishing attempt or not.
How to Secure Your Accounts
Here are some ways to ensure the security of your personal accounts:
– Enable two-factor authentication: Add an extra layer of security to your account by using two-factor authentication.
– Secure your computer: Regularly scan for viruses, avoid accessing unfamiliar websites, and refrain from downloading unknown applications and software.
– Be careful when installing apps on your mobile phone: Limit downloading apps from unverified sources and third-party app stores.
– Avoid sharing your information with unidentified parties: Do not participate in games or activities that require you to provide personal information.
– Set a password for your mobile phone: Use a secure password to protect personal data on your phone.
– Do not use the same password for different addresses: Regularly change your password and ensure it is strong and unique for each account.
– Be mindful of your webcam: Cover your webcam to protect your privacy.
– Be cautious with public Wi-Fi: Think twice before connecting to public Wi-Fi to ensure the safety of your connection.

Follow these guidelines to safeguard your accounts and protect your personal information. Stay vigilant and avoid online account breaches!
Understanding the Security Lock on iPhones: What It Is and How It Works
 Security Lock on iPhones: What It Is and How It Works’>
Security Lock on iPhones: What It Is and How It Works’>Are you aware of the security benefits offered by the security lock on your iPhone’s Apple ID? FPT Shop will share details on how to use this feature and how to maximize its potential – check out the details below!