Smartphones have revolutionized our lives, allowing us to carry a wealth of information wherever we go. However, the risk of personal information leakage from smartphones can be a major concern. If someone else gets a hold of your phone or if you accidentally leave it in someone’s line of sight, they may be able to snoop on your personal information.
That’s why it’s essential to enhance the security and protect your personal data from unauthorized access.
Securing data on Android devices
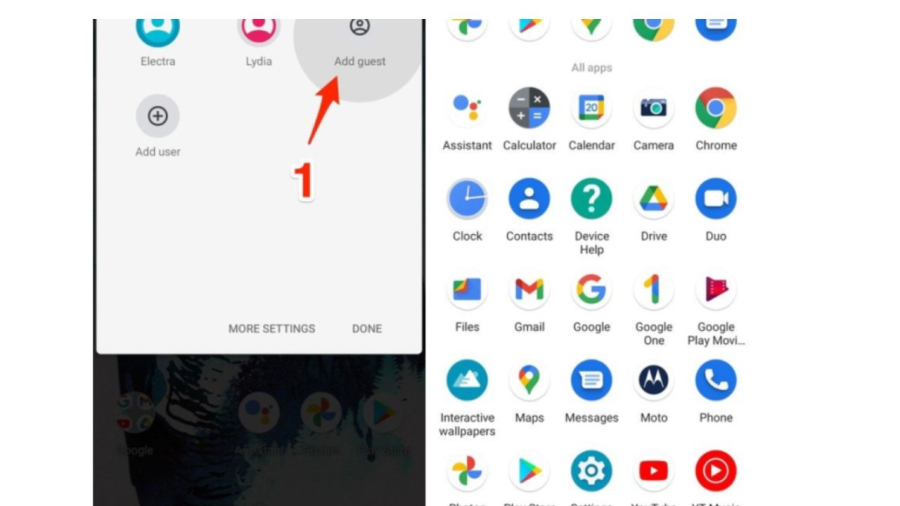
To restrict access on Android devices, you can activate the guest mode or use the screen pinning feature. With guest mode, you can activate it by accessing the Quick Settings, selecting User, and then adding a guest account.
For screen pinning, you can access the Settings, search for the term “Screen Pinning,” and then choose “Ask for PIN before unpinning” to ensure security.
Securing data on iPhones
On iPhones, a similar feature that enhances information security is Guided Access. You can find this feature in Settings – Accessibility – Guided Access. You can set a passcode or use Face ID to ensure the security of your phone.
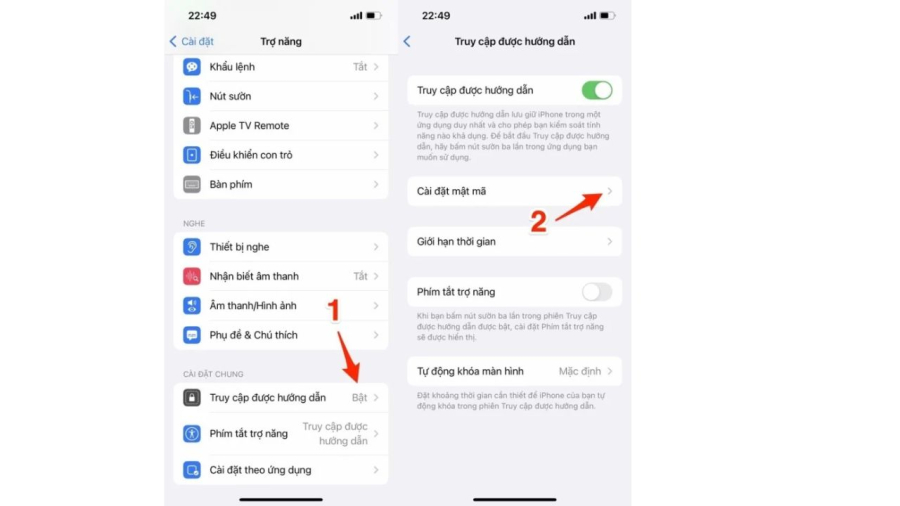
Finally, you simply need to open the necessary app and press the Home button 3 times (or the power button) and then press Start to activate Guided Access. From then on, others will only be able to use the specified app and won’t be able to access other apps.
Additionally, on iPhones, you can limit access to specific apps. You can do this by accessing Settings – Screen Time – Content & Privacy Restrictions and activating this feature.
Here, you can create a password and block access to apps. You can also apply configuration settings to only allow app usage for a limited time each day.
Dealing with suspected information leakage
If you suspect your phone has been tampered with, change your password immediately and log out of all your accounts on your phone. If you still have doubts, contact your phone service provider for assistance.
Furthermore, to ensure the safety of your phone, only install reputable apps and use antivirus software. It is also important to regularly update your device’s software to patch any security vulnerabilities that could be exploited by malicious individuals.
Most importantly, keep your phone secure and protect it from being snooped on: Cover the screen when in public or when someone is nearby, avoid using it in public places, and refrain from using public Wi-Fi for important activities such as banking and payments.