2FA provides businesses with the ability to monitor while protecting their most vulnerable information and networks.

Why is 2-factor authentication – 2FA necessary?
In recent years, we have seen a significant increase in the number of websites that compromise users’ personal data. As cybercrime becomes more sophisticated, companies realize that their outdated security systems are inadequate against modern threats. All businesses and organizations can become victims of hackers.
For individual consumers, the consequences of an attack or identity theft can be severe. Stolen login information can be exploited by criminals to access bank accounts and steal money. The entire balance in a bank account and cryptocurrency can be emptied overnight.

Clearly, websites and online applications need to provide a more effective method of security. Consumers should develop the habit of protecting themselves with something stronger than just a password. For many, that additional security measure is two-factor authentication.
How does 2FA work?
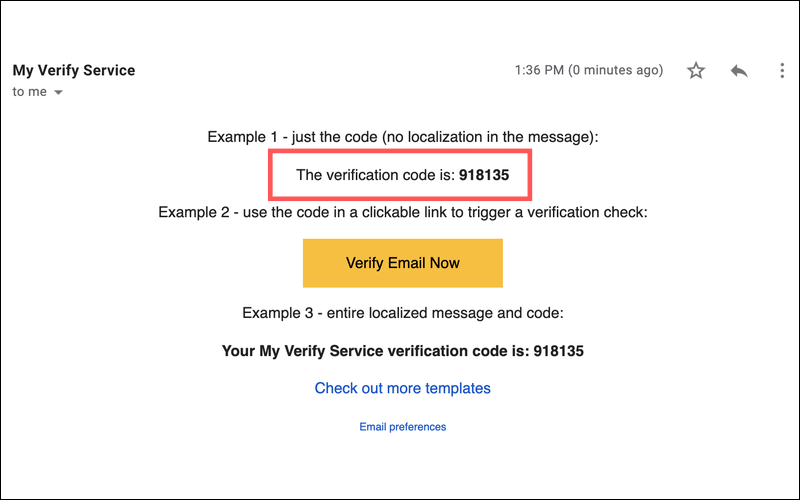
Two-factor authentication is an extra security method before accessing an account. It requires anyone logging into your account to not only have a password but also a verification code. This code can be sent to your email account or obtained from the Authentication app on your phone.
Most current 2-factor authentication (2FA) is also advocated on social networks and modern applications, as well as payment protocols for online systems. This ensures that even if hackers gain access and steal your password, they cannot authenticate the code through personal email and SMS, significantly increasing security.
What are the methods of 2FA verification code?
There are multiple methods to perform 2-factor authentication (2FA). Some of the commonly chosen methods for the second authentication factor to protect accounts and personal information include:
One-Time Password (OTP) via SMS
The user receives a unique OTP through a text message on their mobile phone. This code is only valid for a short period of time (usually less than 1 minute) and must be used to complete the login process. Therefore, failure to enter the OTP sent to the mobile phone into the system will result in a failed login attempt.

One-Time Password (OTP) via Phone Call
This authentication method is similar to OTP via SMS but verified through a phone call. The system calls the user’s registered phone number and provides the OTP through voice. After hearing the code, the user enters it into the system to complete the process.
One-Time Password (OTP) via Email
After completing step 1 of the login process, the system or application will send an email to you, notifying that your account is being verified. If it is indeed you who is logging in, all you need to do is enter the OTP in the email to complete the login process.
Push Notifications
A typical example of this method is Zalo. When you log in to your Zalo account on another device, you enter your account and password. Next, the screen will display a QR code. You use the Zalo app’s QR code scanner on your phone, and then a push notification will appear. The system will ask if you allow access from another device, and if you choose “Accept,” the login process is complete.
Biometrics
The application of biometric 2-factor authentication is being tested for wider application. Recent improvements include verifying a person’s identity through fingerprint, iris pattern, and facial recognition. So far, this is the safest method before hackers find a way to bypass it.
Through Apps
Authentication through apps is a method to verify users’ identities using an app on a mobile device or computer. The authentication code via the app usually changes every few seconds and can only be used once.
What are the advantages of this method?
In actuality, 90% of passwords can be cracked within 6 hours, two-thirds of internet users use the same password everywhere. Professional cyber attacks can test billions of passwords in seconds. It is due to these weaknesses that service providers worldwide have made efforts to create an additional layer of authentication to improve the security of user accounts being hacked.
This additional security step significantly reduces the chances of your account being hacked and provides protection against data breaches. In summary, it has the following advantages:
- Enhances account security
- Protects accounts in case of password loss or theft
- Addresses the weaknesses of using regular accounts and passwords
What are the disadvantages of the 2FA method?

While 2-factor authentication (2FA) has many advantages and offers high security, there are still some disadvantages to 2FA, including:
- Time-consuming during the login process: It takes time to go through an additional layer of security to access your applications.
- Integration: The 2FA security method currently relies on a third-party service provider. As a third-party provider, it may be challenging for businesses to control these external services in the event of an unexpected incident.
- Maintenance: To maintain the optimization of the feature and improve user experience, 2FA requires periodic updates, which can be time-consuming. In addition, some maintenance cases may also be related to ineffective management of 2FA user databases.
How to enable 2FA
Most service providers nowadays upgrade the 2FA authentication system to ensure the best security for user accounts. You can enable 2FA by following the procedures below:
Enable 2FA on Hosting
After completing the website design, your task is to secure the website to ensure its smooth operation and prevent unauthorized access. Usually, the website design service provider will provide you with a login account and password for web management. To avoid having your account hacked and unauthorized access to the website administration area, you need to add an additional layer of account and password protection to the admin directory.
Here are the instructions for adding a password to protect the admin directory.
The following steps are for hosting using Directadmin, but the principle is to create a password for any directory, so you can also follow the same steps for other cPanels.
- Step 1: Log in to your hosting account using the provided username and password.
- Step 2: Click “Password Protected Directories”.

- Step 3: Select the directory you want to protect with a password.
Here, click on “Find a Directory to Password Protect” to find the directory you want to add password protection to.

Select the directory you want to password protect and click “Protect” as shown in the above instructions diagram to add password protection.
Enter a user and password, and confirm the password. Then click on “Protection Enabled” and “Save” to save the information you just created.
Therefore, from now on, to log in to the website administration area, you need to enter the 2FA account and password before entering your account and web administration password. If you encounter any difficulties, inbox 0984966806 (Zalo) for assistance.
Enable 2FA on Facebook
To enable 2FA on the widely-used social network Facebook, perform the following steps:
- Step 1: Log in to your personal Facebook account, then select “Settings”.
- Step 2: Find the “Security and Login” feature to enable 2FA.
- Step 3: Select the “Use two-factor authentication” feature and click “Edit” to enable it.
- Step 4: Choose the verification method you prefer, such as text messages via SMS or security keys. You can also choose options such as a Code Generator or Recovery Codes.
After completing these steps, you have successfully enabled 2FA on Facebook to provide the best protection for your Facebook account. You can now rest assured regarding cases of Facebook hacking and scams that many people currently encounter.
Enable 2FA on Gmail
To enable 2-factor 2FA authentication in Gmail, follow these steps:
- Step 1: Log in to your personal Gmail account and go to “My Account”.
- Step 2: In “My Account”, find the “Security Checkup” feature and click on 2-Step Verification.
- Step 3: Finally, choose the authentication methods such as SMS through your phone, Security Keys, Code Generator, or Recovery Codes.

In addition, users can also choose the special feature of Google prompt. When selecting this feature, users do not need to authenticate with a code; they only need to confirm their choice with a Yes or No. This authentication method is faster, avoiding situations where the code 2FA is read incorrectly, requiring multiple re-entries.
Enable 2FA on Outlook
2-factor 2FA authentication on Outlook is enabled as follows:
- Step 1: The user logs into the Microsoft account to start the authentication process.
- Step 2: Then select the 2-factor authentication and go to the management section.
- Step 3: Continue to verify security by selecting the devices and methods. Then confirm the information you have selected.
With these simple steps, you have authenticated 2-factor 2FA on Outlook.
Conclusion
Now you know what two-factor authentication – 2FA is. It is a very secure way to protect your online accounts. 2FA requires you to enter not only your login information and password but also a verification code sent to your phone or email. This method can accurately identify who is logging in. Even those who have stolen your password cannot log in because they need to go through an additional step to access your account. Operate online safely!
Good luck!